Running SAP CPI Content on SAP NW PI/PO 7.5
Here’s a simple demonstration of how to deploy and run Cloud Integration Content on SAP PI. The integration flow shown below was built in SAP Cloud Platform Integration Suite’s Cloud Integration and is deployable in SAP PI 7.5 S0P8. The integration flow recieves data via an HTTPS adapter and sends it as an email using the configured Gmail ID.
Why would we do this?
There are a lot of reasons why you might want to run CPIS content locally:
- ground-to-ground scenario: you don’t need traffic to go to the cloud since the connected systems all exist in the same network as your on-prem PI/PO instance
- regulatory compliance: privacy, security, or data residency rules may prevent you from sending some interface traffic through the cloud
- you’re writing a blog about how to do this: this is where we fit!
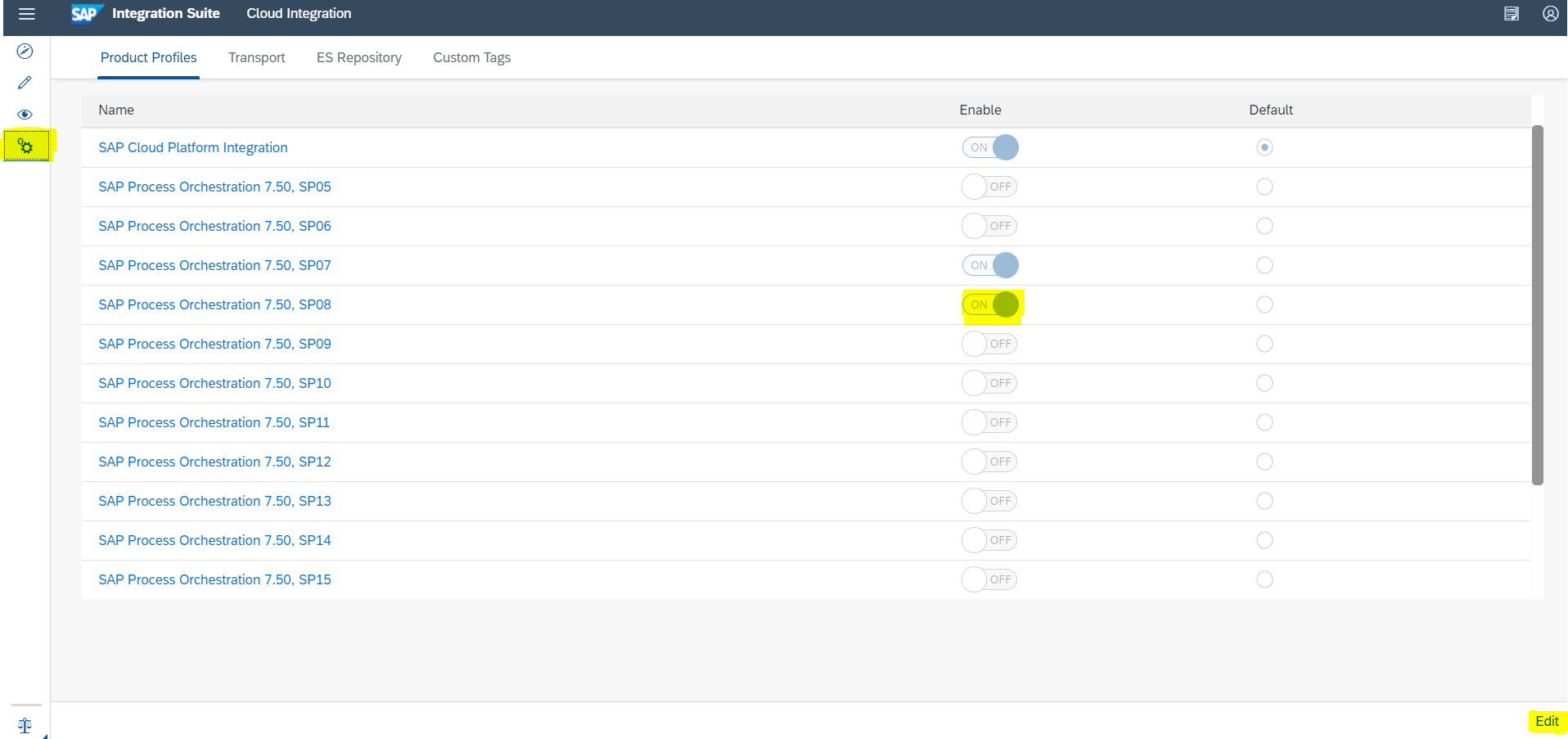
Enable Product Profile in CPIS
Enable the Product Profiles in Tenant Setting according to the SAP PI instance where the Cloud Integration Flow will be deployed. Go to Tenant Settings -> Product Profiles. I’m demo’ing on SAP PO 7.50, SP08 so that’s what I’ve chosen in the screenshot.
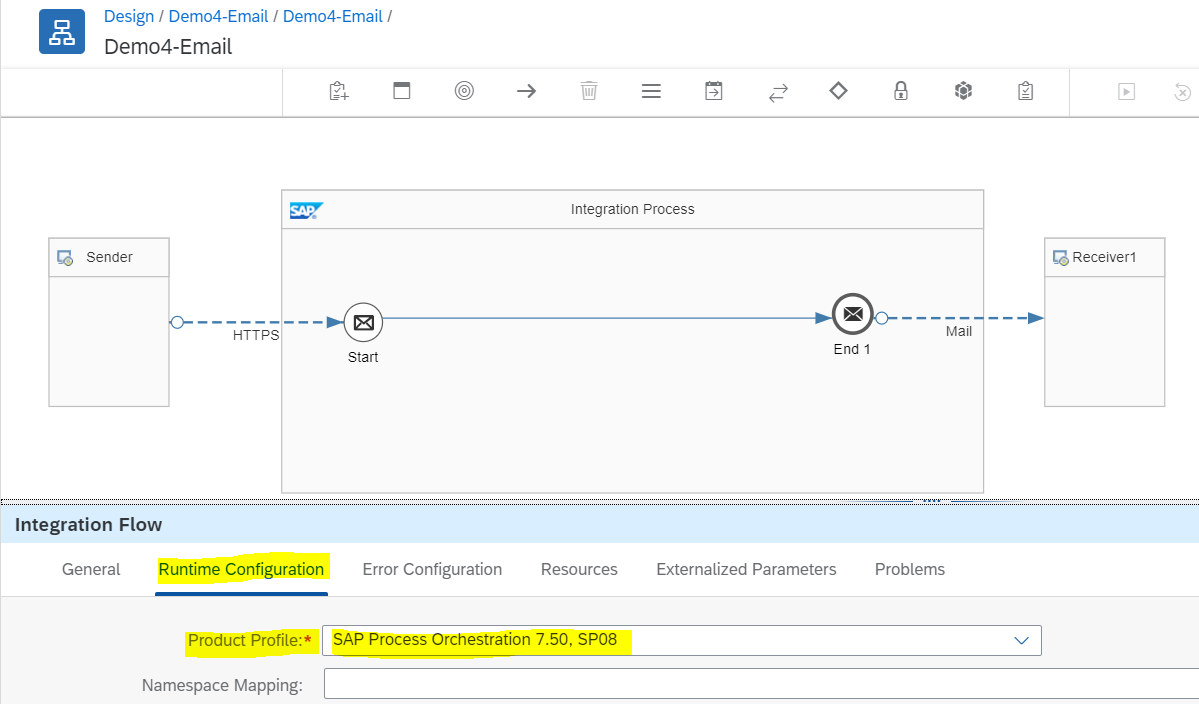
Select Product Profile in Design
On “Runtime Configuration”, you can select the product profile.
Since this iFlow now has a product profile of “SAP Process Orchestration…” you can’t deploy it any longer to SAP CPI Cloud-runtime. The deploy button is still there, but if you click it, you’ll get the below error.
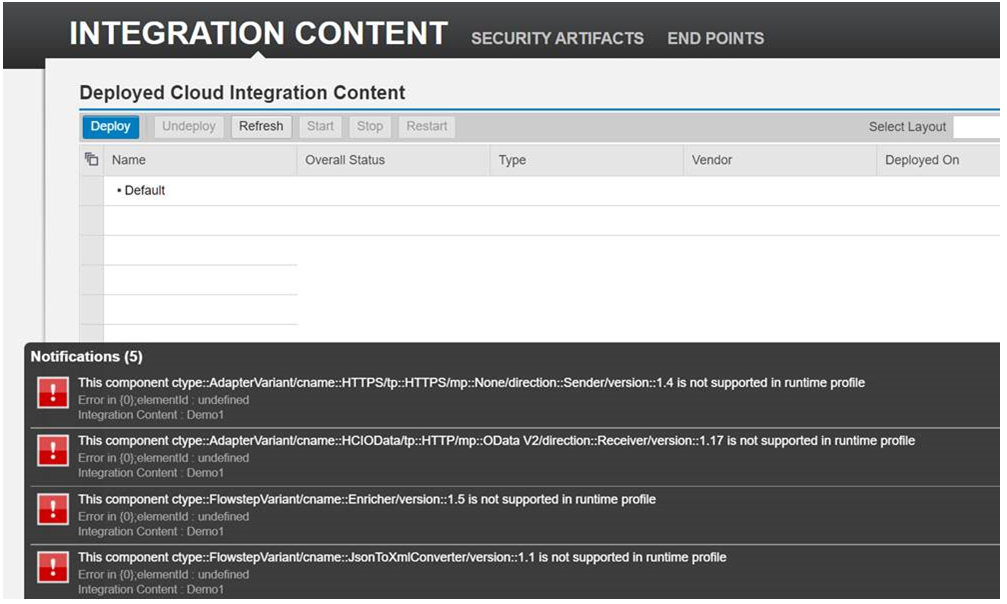
On the other hand, if the correct Product profile is not selected, we will get below error while deploying the Integration content on SAP PI.
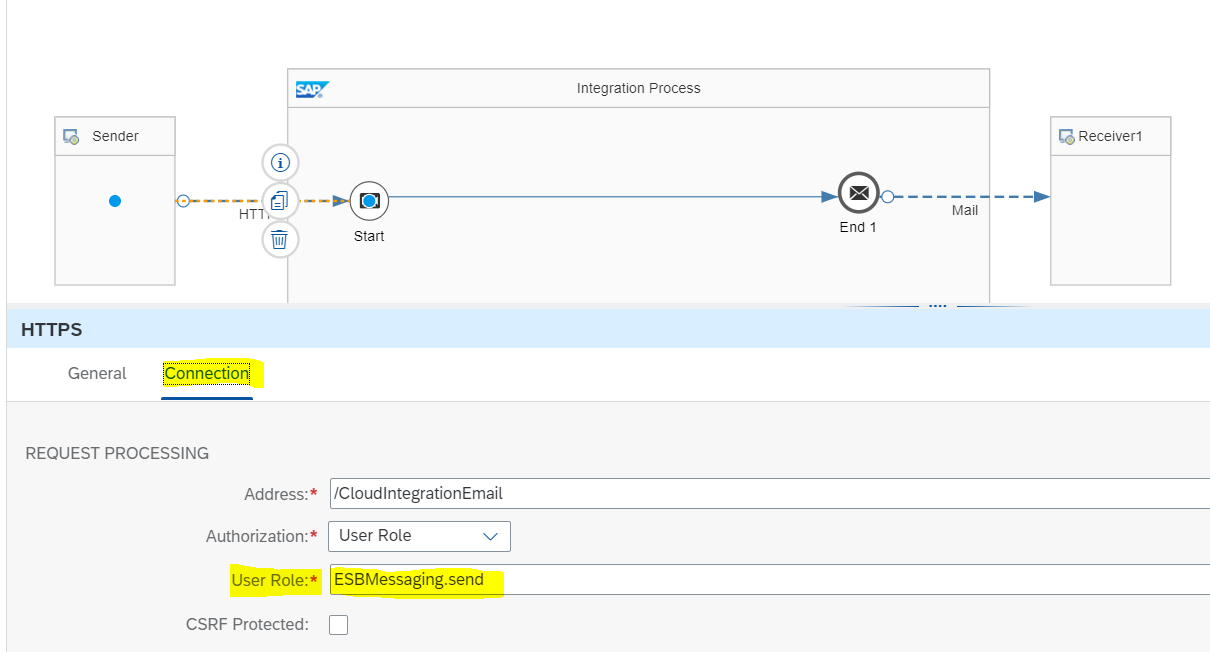
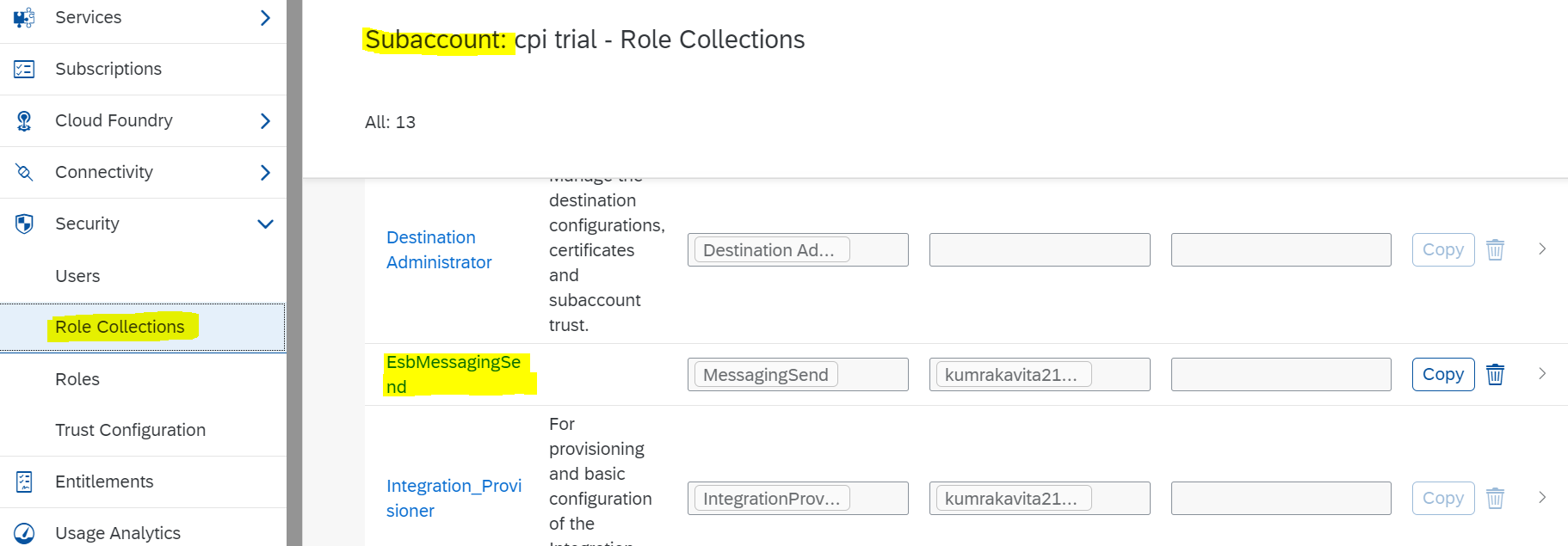
Assign Authorized Role in CPIS Design
As the Sender adapter is HTTPS and we will test the IFlow using external tools such as Postman, we need to add role – ESBMessaging.send to our CPI User.
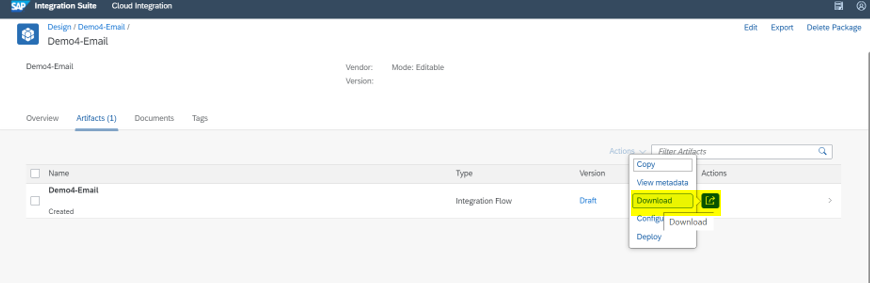
Download and Deploy Integration Flow Artifacts
Download Integration Flow
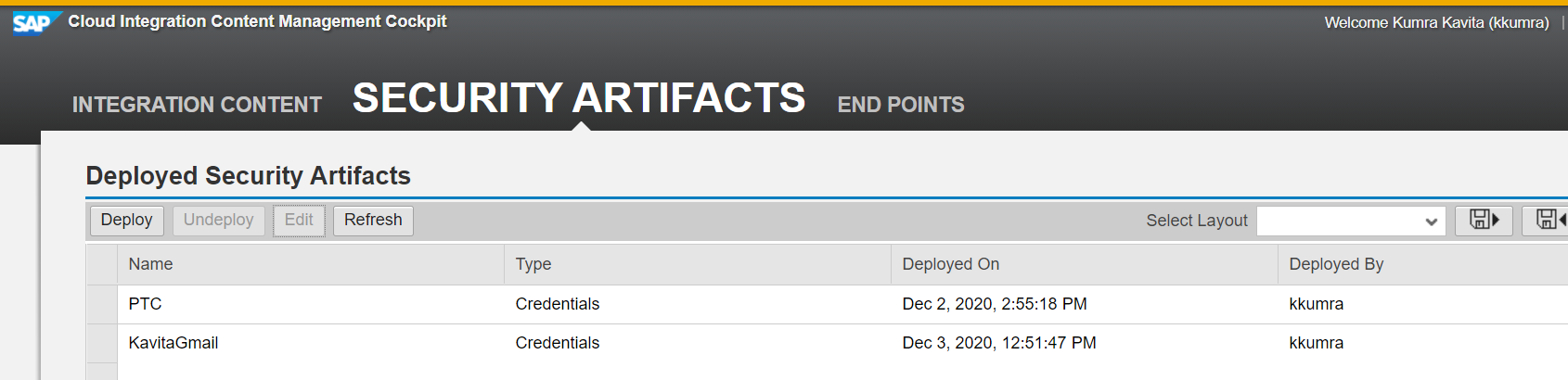
Deploy Security Artifacts
If there are any User credentials configured in the Integration Flow, that must be deployed in the Security Artifacts. Go to Cloud Integration Content -> Security Artifacts ->Deploy
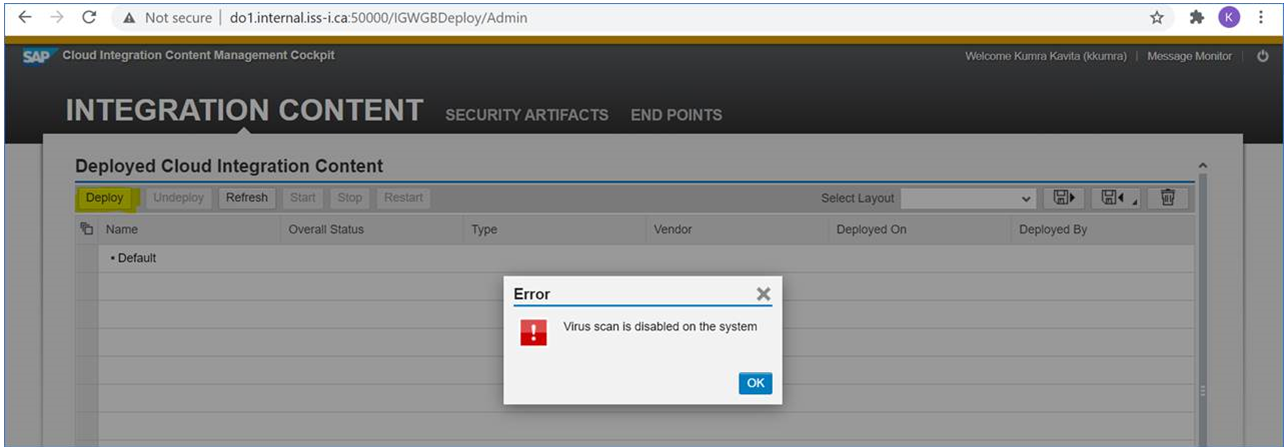
Deploy Integration Flow
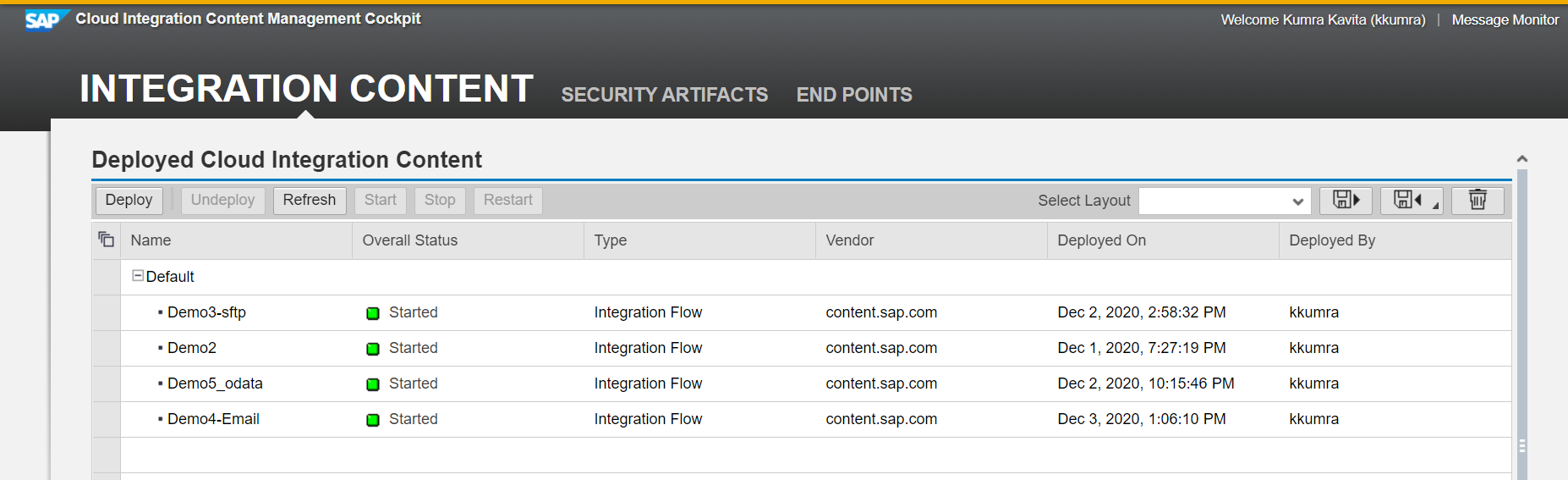
Go to Cloud Integration Content -> Integration Content -> Deploy. Its mandatory to either configure a virus scanner before being able to deploy iFlows in SAP PO or deactivate the virus scanner function completely. You’ll get an error otherwise:
For our POC, I disabled the virus scanner in SAP Netweaver Administrator described in the SAP note https://launchpad.support.sap.com/#/notes/0002266024 which explains:
Application com.sap.aii.igw.gen.build.deploy.app contains the following properties in Java System properties.
- igw.iflow.content.virus.scanner.enabled – To enable/disable Virus scanner for deploying integration content. By default, it’s enabled.
- igw.security.artifact.virus.scanner.enabled – To enable/disable Virus scanner for deploying security artifact. By default, it’s enabled.
Once the Virus scanner is disabled, I was able to deploy IFlow – “Demo4-Email”.
Check PI User Roles
The SAP PI user should have the below roles to deploy the Cloud Integration Content and test it using External tool. These roles are for just for testing purposes and should be severely diminished for run-time service/system users.
| Roles | Description |
|---|---|
| SAP_XI_ADMINISTRATOR | Provides display and modify authorization to view and deploy security artifacts in the Cloud Integration Content Management Cockpit. |
| SAP_XI_CONFIGURATOR | Provides display and modify authorization to view and deploy cloud integration content in the Cloud Integration Content Management Cockpit. |
| NWA_READONLY | Provides display authorization to view monitoring data in SAP NetWeaver Administrator. |
| SAP_XI_APPL_SERV_USER | Provides messaging communication with SAP PI |
Testing
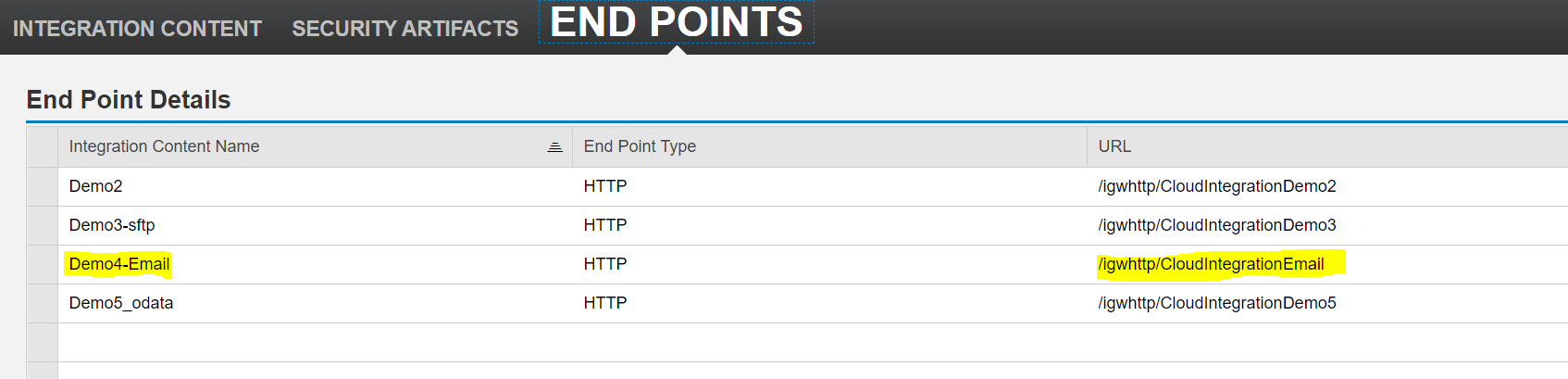
Now, we can test the scenario using Postman. Here’s the format to define the complete URL for Cloud IFlow on PI:
https://{hostname:port}/{endpoint}. The CPI End point can be found from the End Points tab, go to Cloud Integration Content -> End Points
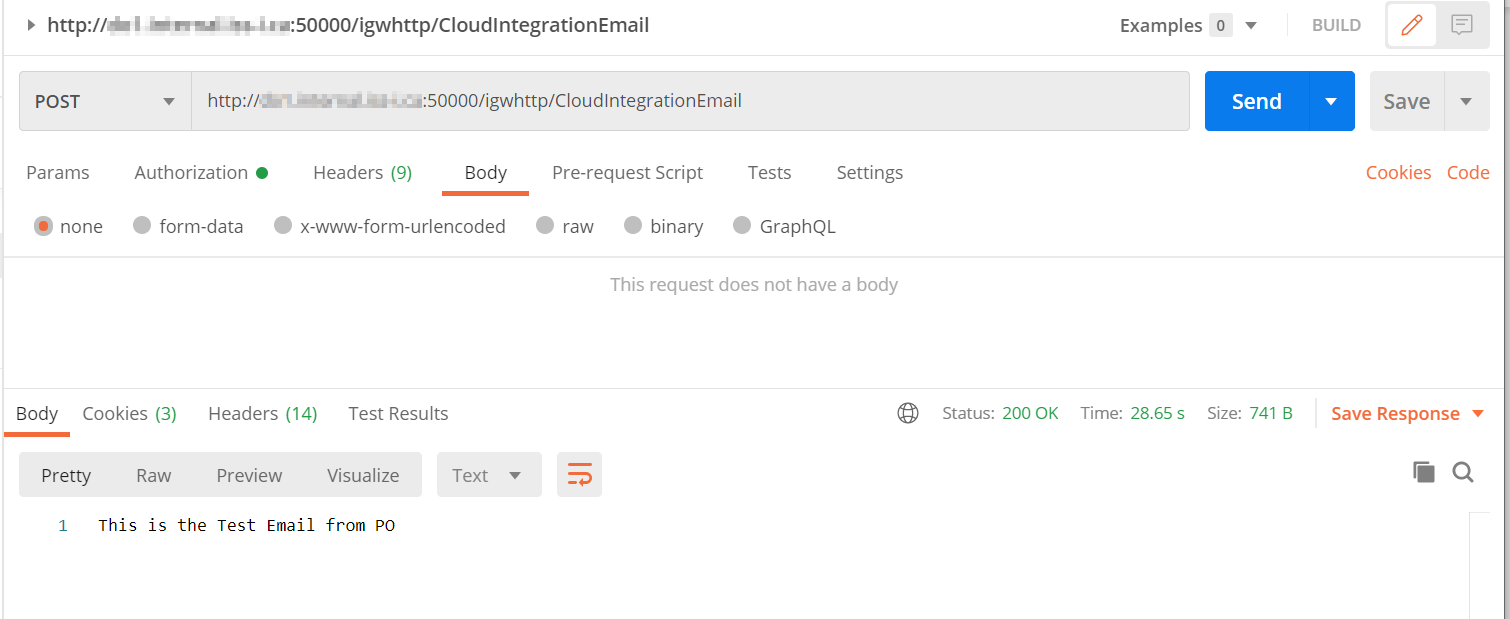
And finally, use the endpoint in your test from a REST client like Postman.